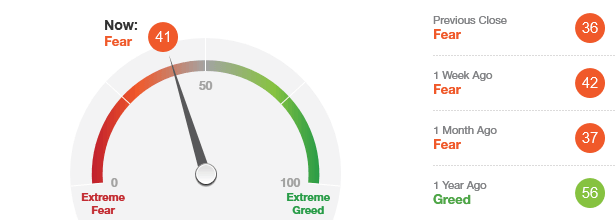
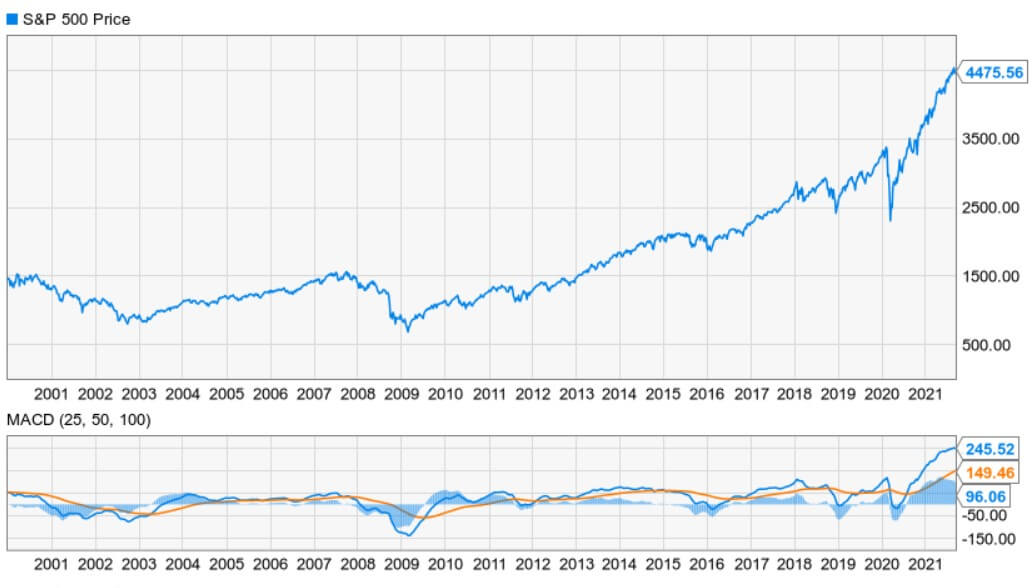
Market Overview
This month’s models are now available.
Pay us $10,000 in bitcoin or we’ll delete all your files
No, we wouldn’t dream of doing that. But there are lots of people who would.
One of them is Maksim Yakubets, the 34-year-old Russian national at the top of the criminal syndicate known as – and we couldn’t have made this up if we tried – Evil Corp.
“Yakubets and his co-conspirators are alleged to have victimized 21 specific municipalities, banks, companies, and non-profit organizations in California, Illinois, Iowa, Kentucky, Maine, Massachusetts, New Mexico, North Carolina, Ohio, Texas, and Washington,” according to the U.S. Justice Department. This “resulted overall in the attempted theft of an estimated $220 million USD, with actual losses of an estimated $70 million from victims’ bank accounts.”

Maksim Yakubets might very well have stolen your money at some point in his criminal career. So if you ever wanted to buy a car like that, good news: You already have. Credit: The Moscow Times
Nobody believes that these crimes – which landed Yakubets on the FBI’s 10 Most Wanted list – are the only ones he ever committed. Also, he’s hardly the only malware attacker out there – just one of the more flamboyant ones.
And, while Yakubets tends to go after organizations, others tend to go after individuals.
Don’t be one of them.
Protect yourself
Fortunately, there’s a whole community of professional paranoids committed to stopping cybercrime. Here are a few of their recommendations.
Assume your current password is awful. The first thing wrong is that “password” is singular. If you use the same password all over the Web, you’re begging for trouble. It should be long, complex and non-sequential. While that means “ABC” and “123” are bad strings, so are “QWERTY” – the first six characters of the familiar Sholes-Glidden keyboard design – and “2580” – the four numerals down the middle column of a 3x4 phone touchpad. The problem is at least as bad as you’ve already guessed; as recently as November 2020, the most popular password was “123456”.
Use two-factor authentication. It’s a bit of an inconvenience, but it’s worth it – particularly if your health or financial records are at stake. Two-factor authentication, or 2FA, involves you entering a password on the site’s landing page, then entering a PIN received via text message before you can access your account information. Depending on the site, you might be able to set up a fingerprint, or facial recognition 2FA layer instead of a PIN.
Secure your device. Nobody should be able to access your computer or phone without a passcode. Aside from that, it’s also important to keep up to date with the latest operating system patches. They are almost always pushed through in response to attempted or successful hacks.
Take a minute before you accept cookies. You’ve heard the term before but, if you don’t know what a cookie is in Web lingo, it’s a tiny block of data a site attaches to your device. It makes it possible to quickly retrieve your login information, shopping cart contents and payment preferences. If you don’t want or need these functions, don’t accept any cookies. If you do, accept only the ones that are fit for your purposes and decline those that might track your browsing history or those that the site extends for the benefit of a third party. It’s also a good idea to dump whatever cookies are already on your device. You can do that by clearing your cache. Without going into detail, you can get started by going into your phone’s Settings menu or, on your laptop or desktop computer, opening your browser and clicking Ctrl+Shift+Del.
Don’t overshare via email. Even if an email appears to be from a brand you trust, don’t respond with any personally identifiable information or anything related to your bank or credit card accounts. “Emails are like postcards. Anyone can see them,” a cybersecurity recently expert told us. One more point: If an unexpected email offers you a link to click, don’t. That would be an invitation to an intruder.
Public wi-fi is just that. While convenient, an internet onramp provided by your local diner could end up causing you more indigestion than the meatloaf. Because as easy as it is for you to get on the wi-fi there, it’s just as easy for hackers to do so as well. Better to connect to the internet via your mobile phone, according to ZDNet. While you could subscribe to a virtual private network – VPN in the biz – that is much better at masking your location geographically than protecting you from cyberattacks.
Stop using credit and debit cards. That doesn’t mean stop spending money – that’s another article – but they’re dangerous to flash around online. “The system of credit card use is outdated and not very secure at all,” according to PC Magazine. “Use Apple Pay or an Android equivalent everywhere you can. There are tons of choices when it comes to apps. … Setting up your smartphone as a payment device is typically a simple process. It usually starts with snapping a picture of the credit card that you'll use to back up your app-based payments. And setup pretty much ends there; you're ready.” The major advantage is that the security code is a static three- or four-digit number on your cards, but is a single-use string for payment apps. It’s like throwing out your Visa and getting a new one after every transaction.
Don’t be a victim. Sorry, there’s no other way to put it. If you believe the federal government will have you arrested if you don’t respond to this email, or that you have $1,000 credit with Amazon, or that a Nigerian prince needs your help transferring his money from one account to another and is willing to pay you for your assistance, then you’re being naive. By the way, this kind of scam – called phishing or social engineering – is older than the internet and is just as likely to reach you via the phone. “The IRS does not call you – ever,” our cybersecurity experts tells us. “They do all their correspondence by mail.”
Who’s watching your money?
Financial services firms have been provided a litany of regulations for how they are to go about protecting your money. That’s good news for you.
“For financial services companies in the US, laws addressing cybersecurity expectations and requirements include the Gramm-Leach-Bliley Act (GLBA), the Bank Secrecy Act, the
USA PATRIOT Act, the identity theft red flags rule, and Sarbanes-Oxley. Banks are regularly examined on their compliance with these rules, as well as published information security guidelines and bulletins,” according to British-based global law firm Latham and Watkins. “As a result, the financial services sector in the US is among the most aware, most organised, and most sophisticated industries facing the cyberthreat …”
And it would be great if L&W ended the sentence right there.
“… yet it is simultaneously amongst the most targeted.”
Broker-dealers and investment advisors are subject to the authority of the Securities and Exchange Commission, which concentrates its cybersecurity operations in the Office of Compliance Inspections and Examinations. It is OCIE’s duty to identify cyber-risks stemming from firms’ auditors and other third-party vendors. The operative law is Regulation SP, which requires firms to safeguard the confidentiality of customer records. It’s important to note that OCIE offers only guidance and that there is little in the way of concrete rules governing financial firms’ cybersecurity.
Still, there are best practices as identified by the Financial Industry Regulatory Authority, an industry self-regulating organization chartered by the SEC. FINRA’s guidance centers around:
- Vulnerabilities specific to branches as opposed to headquarters,
- Asset inventory exposure,
- Phishing,
- Insider threats,
- Privileged user controls,
- Data loss prevention and
- Third-party risk.
There is also a list of practices related to the underlying technology. Of course, executive and management support is as critical to any cybersecurity initiative, just as it is for any other initiative. These systems are only as useful as the people sitting in the chairs, so training is a key consideration, as is penetration testing – having white-hat hackers try to infiltrate the system before the black-hats find the way in.
Even so …
What we hope we’ve provided you today are some concrete steps you can take to mitigate your chances of having your money or your identity stolen online. Mitigation is not the same as elimination. We would never pretend to offer you that.
There are other habits you could adopt to burrow even deeper into cybersecurity. Chrome is not the only browser, nor is Google the only search engine available. SMS isn’t the only way to exchange text messages. There are inherent risks in using all of those, and they have competitors whose key value proposition is that they insulate users from hacks that can come via those channels. You probably don’t need to go that far, but we wouldn’t blame you if you did. There are also things you could be doing in the social media realm to make sure that Facebook, Twitter and their peers don’t know more about you than you care to tell them – and that you take steps to make sure they don’t share your data with their advertisers and whoever else.
Still, what we offered you is more than just security theater. If you follow these protocols, the cybercrooks are much more likely to target the next guy.
And the same goes for your financial professionals. Sorry, but there’s no way to guarantee that even the most diligent firm won’t get hacked but, if the people there are doing everything they can to harden their systems against attack, odds are it will be some other firm’s vulnerabilities that get exploited.
What is your financial advisor doing to keep your accounts and data safe? If you don’t know, maybe you should ask.